Computer security can’t be stressed enough in law firms. It’s tempting to think you personally don’t really have to pay attention to “security stuff,” or that your firm is “too little” for bad guys to be interested in. But you’d be wrong. As with so many things, size is not important when it comes to client data security and confidentiality.
So while you may be tempted to face-plant or claw your eyeballs out from boredom when security issues come up, I urge you to resist. Basic law firm computer security practices aren’t just for the experts — they’re for everyone.
In Case You Aren’t Convinced
CryptoLocker, one of the bad guys currently circulating, is a chilling reminder of what’s out there waiting for the unsuspecting and unprepared — and what may yet be coming. It is a new variation on an old malware theme and it’s a true horror.
If you haven’t heard about it, there’s an excellent primer (including remediation steps) at Bleeping Computer: CryptoLocker Ransomware Information Guide and FAQ.
Essentially, a workstation can be infected by way of an email with a malicious attachment or link. The email purports to be a support request from UPS or FedEx, or a payroll company, or a similar business that law firms use regularly. Except, of course, these emails aren’t really from those businesses. If someone in your firm opens the attachment, the infection takes hold. There is no indication of infection until the damage is done. Files are encrypted, with no way to un-encrypt them without either paying a ransom to the bad guys or restoring from backup. What’s even worse than having the workstation data encrypted is this: The virus is network aware and will also encrypt data on ALL MAPPED NETWORK SHARES (sorry about the shouting).
You won’t even know until this notice pops up on the infected workstation, and by then it’s too late:
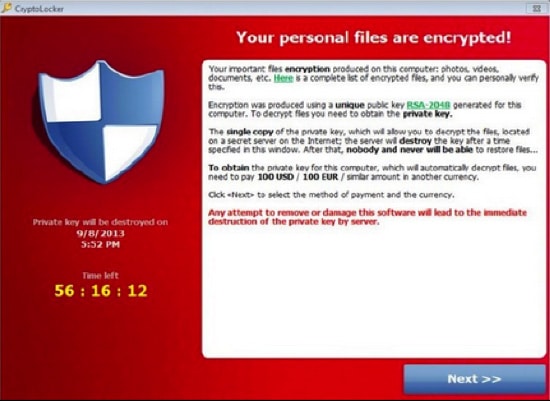
The timer is real. You have three days to either pay up, or restore from backup. (Keep your fingers crossed that your backup is current and also uninfected — but even if it is, restoring may take a considerable amount of time, depending on the data involved.)
Once the countdown clock reaches 0:00, the bad guys toss away the necessary private encryption key and even they can’t retrieve it — your files are permanently encrypted.
If you’re frightened, you should be. But it won’t do any good to stop there. Here are steps you can take beyond the basic security.
- Keep all software patched and current, especially your operating system. (Firms hanging onto Windows XP are really flirting with danger.)
- Keep your antivirus software up-to-date, and not just on workstations because servers need protection, too. Monitor it regularly to ensure it is operating as expected.
- Ensure workstations have minimal local privileges. Local admin is a no-no unless certain software requires it.
- Uninstall Java and Flash (unless you run software or access websites that absolutely require it — if so, be religious about applying update patches).
- Have a security policy in place. Train all lawyers and staff on the policy; refresh yearly.
And always, always keep the following in mind: None of this would have protected against CryptoLocker at Zero Day (before antivirus software was updated to recognize it). It would have slipped past all defenses except for the last and best defense: a skeptical end-user. In other words, you and your staff.
Stay Skeptical Out There: More Safety Tips
Here is some additional advice to help you and your valuable client data stay safe.
Never let your guard down. Emails with infected attachments or links often come from recognized sources. So if you aren’t expecting the email, don’t just click on it. Call the person it came from, if you know them. If it’s from a company, even one you do business with, think long and hard about it. How would they even know your email address? It’s not something you would normally provide when using a courier or dealing with support. The bad guys are counting on you feeling comfortable (or curious) enough to click. They make it look good and real to give you that level of comfort. Always start from a position of distrust. This must apply to everyone in the office.
Hover over links and email addresses without clicking. Hovering will pop up the real underlying email address — the place you will really be taken to if you click. Give it a try by hovering over a link in one of your emails now. The underlying address should always match the typed address.
Don’t trust an attachment by its icon. Just because the icon appears to be a PDF, that doesn’t mean it really is one, and just because a file attachment name ends in .pdf, that doesn’t mean it really is one. By default, Windows is set up to hide known extension types, such as the .doc extension for Word documents and .pdf extensions for Acrobat files. (Don’t ask me why Microsoft has chosen this default, just know that this is something the bad guys can take advantage of.) That means an infected .zip file could appear to you as a .pdf file. At the very least, hover over the links to make sure the underlying file really is what it says it is. But it’s best to make sure your computers are configured to show all file extensions. Microsoft has straightforward instructions on how to do this here: Show or Hide File Extensions.
Don’t let antivirus software give you a false sense of security. No antivirus software catches everything, and some infections are so new that nothing can catch them before they start wreaking damage. I tend to think of antivirus software like police — valuable for catching the bad guys after the crime has been committed.
In addition to those basic security steps and remaining perpetually on guard, speak to your tech guru or IT staff about the following security measures.
Prohibit program execution from your AppData folder. (Details for doing this are in the CryptoLocker link above.) This workstation change would have stopped a CryptoLocker attempt in its tracks (along with another bad guy, ZBOT). Since it can have unintended program consequences, it’s best to let a techie do it so they can remove it if it causes problems. (I run a lot of software and have instituted this change and haven’t noted any issues on my workstation.)
Don’t let .ZIP, .RAR, .EXE or .SCR files into your email. If they never arrive at your desktop, you won’t be tempted to click on them. Have your techie configure your email to block all malicious file types. (Configure the email server if you have one, or every workstation if not.) There is never a reason for a sender to email .exe (programs) or .scr (screensaver) files to you. If someone tries to send you a .zip or .rar (compressed file) and you’ve blocked them, let the sender know they’ll have to send you the files some other way (native format is best).
Don’t let anyone plug a USB drive or external hard drive into a USB slot on any workstation. Disable your USB ports if practical. At the very least, disable AutoRun. (See the instructions here: How To Disable AutoRun / AutoPlay In Windows 7 & Windows 8.) That way, the mere act of plugging in the drive can’t trigger infection. This is something you’ll probably want your techie to handle also.
And stay safe out there.
Vivian Manning is the IT Manager at Burgar Rowe PC in Barrie, Bracebridge and Cookstown, Ontario. Prior to moving into IT, Vivian practiced law at Burgar Rowe, primarily in the area of municipal land development, with a total of 17 years in private practice before switching to the IT end of the law office. She currently indulges her love of teaching tech through her blog Small City Law Firm Tech, where she provides “tips of the day.”
More Power User Tips
- Right-Click Your Way to Computing Paradise
- Copy and Paste Made Easy
- Don’t Touch That Typo!
- Outlook’s InfoBar: Under Your Nose, at Your Command
- The Importance of Being Trained
Illustration ©iStockPhoto.com




















