To be honest, we’re feeling fatigued by the steady stream of data breach notifications and the hyperventilating over hacker schemes. As with the nonstop news of political scandal, there’s only so much outrage you can absorb before you must tune out. Vigilance is exhausting. Unfortunately, it is also very necessary.
So, since there is no point in feeling both exhausted and helpless, we asked the practice management technology experts: What can a law firm do to make a hacker’s job harder these days?
Here’s advice you can use to fight the good fight — and stay out of the cyber-crosshairs — from Heidi Alexander, Sheila Blackford, Andrea Cannavina, Tom Lambotte, Sharon Nelson and John Simek, Lee Rosen and Emily Worley.
Sharon Nelson and John Simek: Practice Safe Browsing
Practicing safe computing is a constant battle. It seems like the “bad guys” are always thinking of new ways to compromise your machine and get access to your data. You can improve your cybersecurity posture by practicing safe browsing. Start by using Chrome as your default browser. Next, add some extensions to block certain activity. Some of our favorites include:
- DuckDuckGo Privacy Essentials to block hidden trackers and protect your privacy.
- Privacy Badger from the EFF to block spying ads and hidden trackers.
- AdBlock to block YouTube, Facebook and ads everywhere else on the web.
- IDN Safe to block internationalized domain names to prevent you from visiting probable fake sites.
- Windows Defender Browser Protection provides an additional layer of protection when browsing online.
Finally, install the PassProtect extension from the Chrome webstore, which alerts you if your password has been previously discovered in a data breach. It is powered by the database of Have I Been Pwned?
Sharon D. Nelson (@SharonNelsonEsq) and John W. Simek (@SenseiEnt) are President and Vice President of Sensei Enterprises, Inc., a digital forensics, legal technology and cybersecurity firm based in Fairfax, Va. They have written 16 books published by the ABA, including “The Solo and Small Firm Legal Technology Guides” and “Encryption Made Simple for Lawyers.”
Lee Rosen: Don’t Lock Yourself Out of Your Own Data
One problem with cybersecurity is that sometimes the data is more secure from you than it is from the hackers.
How likely is it that you’ll lock yourself out of your data? Do this drill and find out:
- Pretend you’re on Bali at the beach. A tsunami hits. You’re tossed up on top of a palm tree and survive. But your iPhone, your MacBook and those belonging to your spouse are washed away. You’re cranky, wet and without any devices.
- Fortunately, you find some cash on the body of someone not so lucky and use it to buy a new iPhone from the hut on top of the big hill. You’re ready to roll.
- Unfortunately, you previously protected 1) your iPhone with two-factor authentication, 2) your passwords with 1Password, and 3) saved your banking and Google two-factor codes with the Authy app.
- Get access — go!
Hints: I hope you’ve authorized someone else’s phone to receive your authentication codes from Apple before the wave hit. You’d better have stored your 1Password Secret Key somewhere accessible and not in your luggage. Also, if you haven’t installed Authy on a friend’s device as a backup, then prepare to wait 48 hours for two-factor code access. If your Authy email address is two-factor protected prepare to wait longer. If you’re using Google Authenticator — UGH!
Lee Rosen (@LeeRosen) grew his North Carolina family law practice and sold it. He travels full time while helping lawyers grow their practices. His blog at Rosen Institute is an ABA Blawg 100 Hall of Fame honoree. He is a recipient of the ABA James Keane Award for Excellence in eLawyering.
Heidi Alexander: Be Spoof-Proof!
Believe it or not, as I sat down to write this tip, I received a spoofed email from a colleague. It looked like it was sent from someone in my organization, but in fact, it was sent from a different email address. As you can see below, there were a number of telltale signs of spoofing. Based on my understanding of it, this was an attempt to get me and other recipients to trust this email address so that it could later fill my inbox with spam advertising, capture my personal information or even impersonate me.
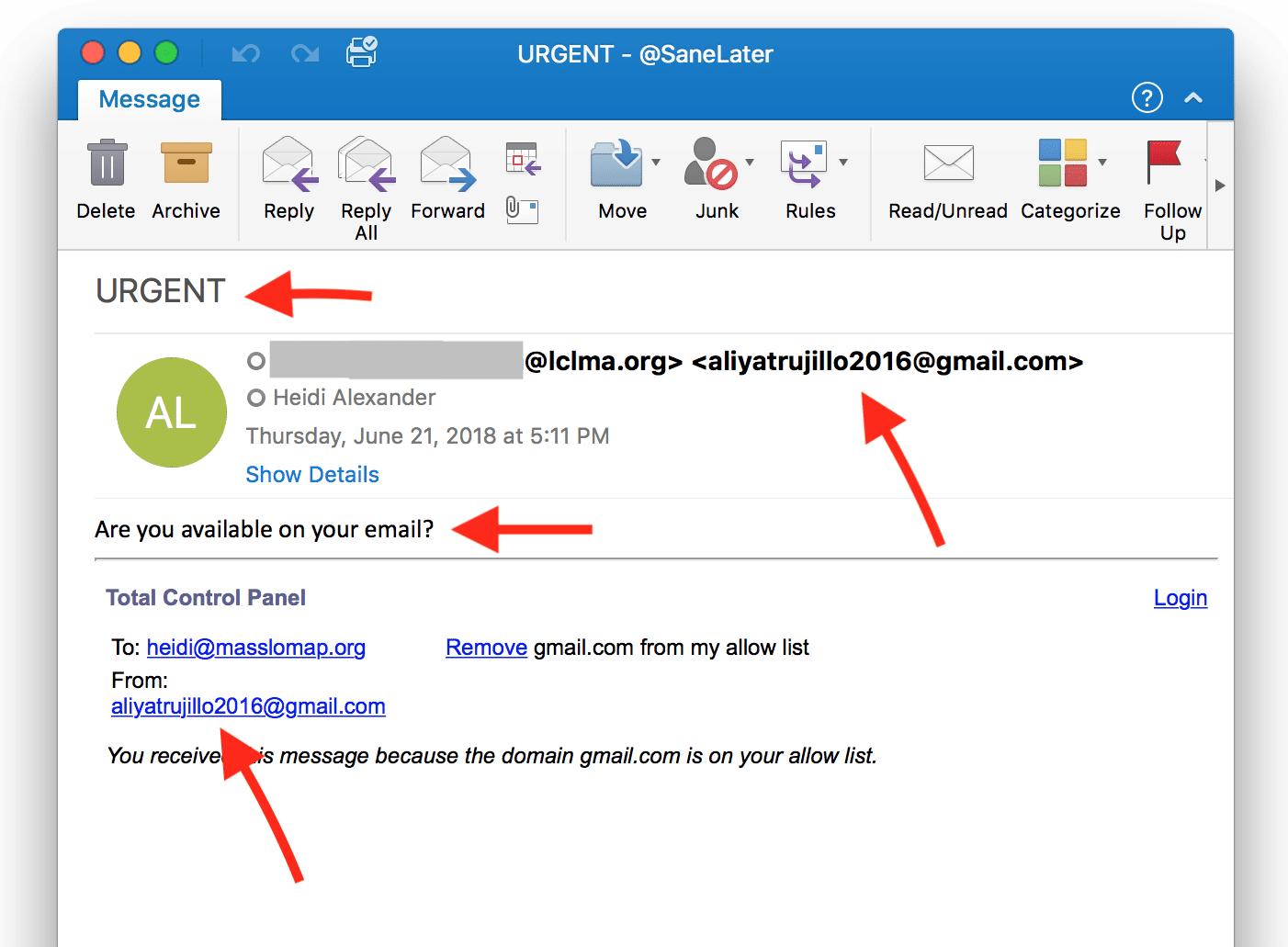
The lesson? Be suspicious of every email you receive.
- Always review email message headers and check email addresses by hovering your mouse over the address. Do the same with links before clicking them.
- Be wary of any email that expresses urgency.
- Do not provide any confidential or personal information when requested to do so via email, particularly if you were not expecting to do so.
Lastly, the best protection against any unwanted access to your data is using strong passwords.
It continues to amaze me that every year the most commonly used passwords remain unchanged and include “123456,” “password,” “qwerty” and “admin.” If you are using one of those passwords, please stop now! Passwords must be strong and unique. You can test the strength of yours at howsecureismypassword.net.
When you use the same username and password for multiple services, if one service is compromised, then all of your services may be compromised. To check whether a service you’ve used has been compromised, go to Have I Been Pwned? If so, change your passwords associated that username and email.
The best way to create unique passwords for each service you use — and to remember those passwords — is with a password manager such as 1Password or LastPass.
Heidi S. Alexander (@heidialexander) is Deputy Director of Lawyers Concerned for Lawyers, where she also leads the Massachusetts Law Office Management Assistance Program (LOMAP). She is the author of “Evernote as a Law Practice Tool” and serves on the ABA TECHSHOW Planning Board and the Massachusetts Supreme Judicial Court’s Standing Advisory Committee on Professionalism.
Tom Lambotte: Monitoring the Dark Web
Did you know that in a recent report by cybersecurity company RepKnight, they analyzed the dark web footprints of the top 500 U.K. law firms and discovered the details of over 1 million hacked, leaked or stolen credentials being circulated online?
The vast majority of these credentials were exposed through “third-party breaches” — a data breach from another website or system unconnected to the law firm, where their employees had signed up using their work email address. These breaches are not the fault of the law firm, and there’s no suggestion that the firm’s networks have been hacked.
So the truth is the data is out there, and you’d be shocked at how many of your firm’s emails and passwords are being sold on the dark web — likewise for other sensitive information.
Another relevant data point is in the new guidelines issued last summer by the National Institute of Standards and Technology. NIST guidelines often become the foundation for best practice recommendations across the security industry and are incorporated into other standards. One of the new guidelines recommends to only force a password change when there’s been some kind of security breach. This goes against what they recommended for 20 years. But otherwise, the changes we make are often incremental; when forced to switch out our passwords every 90 days, people just swap out one character. That makes the bulk of passwords ineffective; this practice harms security rather than helping it.
The key in the new guideline is “only force a password change when there’s been some kind of security breach.” So how do you know when there’s a been a security breach? This is where a dark web monitoring service comes into play. Such services scour the dark web for your firm’s information and alert you when something is found. It acts like a “burglar alarm” for your data, giving you early warning of potential breaches, and demonstrating that you’ve taken proactive mitigating steps to minimize the effects of any breach.
We are offering a free scan as a public service to help firms discover if they are at risk here.
Tom Lambotte (@LegalMacIT) is CEO of GlobalMacIT, a company specializing in providing IT support to Mac-based law firms. Tom is the author of “Hassle Free Mac IT Support for Law Firms” and “Legal Boost: Big Profits Through an IT Transformation.”
Emily Worley: Five Steps to Proactive Prevention
When was the last time you had your teeth cleaned, eyes checked, vehicle serviced, or house inspected for termites? What about your office? How long has it been since you had a wellness check, especially for hardware, software, networks and mobile devices? If you can’t remember, you are not alone. Welcome to human error.
Hackers and crackers are well aware of how human error plays into intentions. Study after study shows over half of entities know their weakest link is employees. That’s why many, including law firms, are being proactive by implementing five objectives to thwart hackers and crackers:
- Remain current on technology best practices. Establish cybersecurity policies.
- Require hands-on training for all employees.
- Integrate preventative care or best practices.
- Test infrastructure and conduct a regular audit.
- Consider cyberinsurance.
Although preventative care does not always prevent problems, malfunctions or disasters, so is the case with technology. However, consistent proactive decisions and implementation will lessen the chances of you or your office becoming another statistic.
Emily Worley (@pmaptechie) is the PMAP Assistant to the South Carolina Bar Practice Management Assistance Program, where she assists the PMAP director in providing practice management and technology assistance to South Carolina Bar members.
Andrea Cannavina: Stop Distracted Clicking
Pay attention. Don’t distractedly click. On. Anything.
If you train your brain to lift your hand from your mouse or device when you are not paying 100 percent attention, you will be less likely to have that one “oops” moment that ruins the rest of your day (and perhaps even week).
Also, if a pop-up pops up, make sure to hit the red X in the corner of the Windows pop-up screen and nothing within the pop-up itself. Those pop-up boxes can be programmed to do anything once clicked … including instantly download a file to your computer.
That’s two tips. PAY ATTENTION TO THE FIRST ITEM AND DON’T DISTRACTEDLY CLICK. Remember, distracted clicking kills your devices, your day and even your reputation.
Andrea Cannavina (@AndreaCan) is CEO of LegalTypist and Director of the Virtual Bar Association. She helps lawyers, legal administrators and companies that service the legal industry better understand the role of technology and use of the web in the daily practice of law.
Sheila Blackford: Time to Step Up Your Data Security Game
Law firms need to step up their data security game and respond with equal measures of vigilance and common sense.
You may be congratulating yourself for avoiding clicking on pop-up ads and opening unexpected suspicious attachments. This may not be sufficient, however, as this real-life story of a small Oregon law firm shows.
The law firm posted an ad on Craigslist looking to hire a new legal assistant. Soon, job candidates began emailing their resumes and cover letters — and one of them sent an attached Zip file. Believing the file must certainly contain the applicant’s resume and cover letter, the lawyer never hesitated before clicking on the attachment and downloading it to the law firm’s server. Immediately, a ransom note appeared on his computer screen saying that all files had been encrypted and $750 in bitcoin needed to be paid within four days or the files would be destroyed.
The note gave instructions on how and where to send payment while a timer ominously gave the countdown of time remaining to act. The lawyer alerted everyone in the office to stop working on their computers and quickly unplugged the server to isolate it from the other office computers.
The firm decided to pay the ransom to decrypt the data but had great difficulty purchasing bitcoins. The value of the bitcoins fluctuated after transferring them to the attacker who then emailed to say the bitcoins were insufficient. This caused further delays and increased frayed nerves in recovering 99 percent of the firm’s data. Although some of the missing data was on an off-site backup drive, it wasn’t fully up-to-date. In the end, the firm lost about two months of data from a number of people at the firm.
Here are some of the wise changes implemented by the firm:
- Using a cloud backup system but not keeping their computer attached to the backup except when performing a backup.
- Developing and following a written policy on data security, including the instruction to never accept and open Zip files, regardless of the sender.
- Conducting regular training meetings to review the data security policy and remind staff to never open unsolicited emails or click on unexpected attachments.
- Requiring that all large digital files be sent and received via thumb drives or CDs that are first scanned by an updated antivirus program.
- Maintaining all computers on an updated operating system with the same antivirus protection.
- Ensuring that all devices containing client file information are protected by strong passwords that are changed every 60 days.
It is a good idea when hearing stories about security breaches to think about how you might avoid a similar attack. Educate yourself and your staff about the warning signs. Realistically assess the weaknesses in your computer security and fix them.
Sheila M. Blackford (@SheilaBlackford) is an attorney and Practice Management Advisor for the Oregon State Bar Professional Liability Fund. She is the author of the ABA book “Trust Accounting in One Hour For Lawyers,” co-author of “Paperless in One Hour for Lawyers,” and a past Editor-in-Chief of the ABA’s Law Practice magazine. She writes the Just Oregon Lawyers Blog.
Illustration ©iStockPhoto.com
Subscribe to Attorney at Work
Get really good ideas every day: Subscribe to the Daily Dispatch and Weekly Wrap (it’s free). Follow us on Twitter @attnyatwork.

















